Fort Firewall 3.15
Fort Firewall 3.15 Free Download is a robust and user-friendly firewall application designed to enhance the security of computer systems by controlling network traffic and protecting against unauthorized access.
Fort Firewall 3.15 Description
It provides various features tailored for novice and advanced users to manage and monitor network activity effectively. Fort Firewall is a powerful and versatile firewall solution that balances ease of use with advanced features, making it suitable for a wide range of users and environments. Its robust traffic control, real-time monitoring, and comprehensive security features effectively defend against network threats and unauthorized access.
Fort Firewall 3.15 helps you have more control over your system’s Internet connections and you can control how certain programs use bandwidth and specify whether or not each program can access the Internet. All the features provided in Fort Firewall 3 are designed to simplify the way you interact with the system’s default firewall and do not necessarily add anything new but rather provide all the necessary settings in one place and a transparent and simple user interface.
Features Of Fort Firewall 3.15
1. User-Friendly Interface
- Intuitive Design: Offers a clean and intuitive interface that simplifies the setup and management of firewall rules and settings.
- Dashboard: Centralized dashboard for monitoring real-time network activity and system status.
2. Traffic Control and Monitoring
- Network Traffic Management: Allows users to control incoming and outgoing network traffic based on predefined or custom rules.
- Real-Time Monitoring: Provides real-time monitoring of network connections, displaying detailed information about active connections, including IP addresses, ports, and protocols.
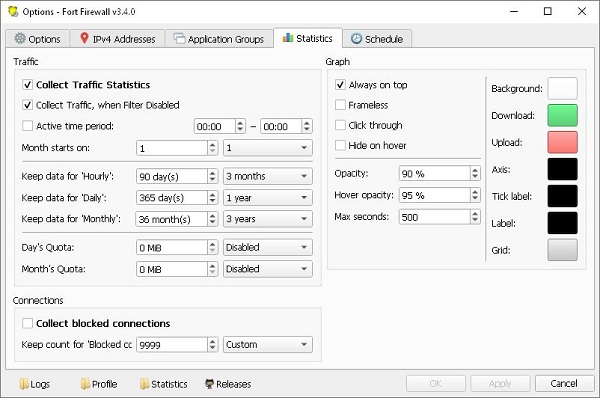
- Bandwidth Usage: Tracks and reports on bandwidth usage, helping users manage and optimize their network resources.
3. Rule-Based Filtering
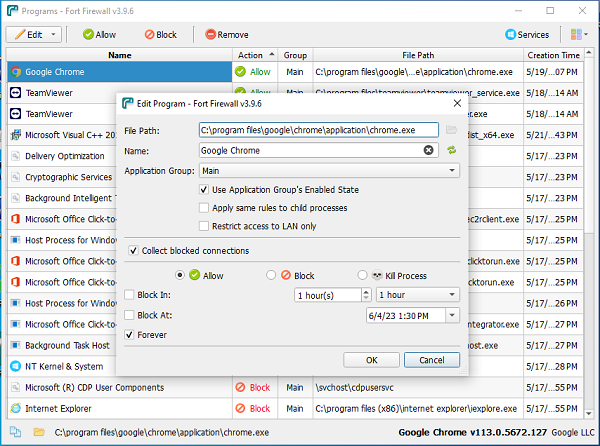
- Custom Rules: Enables the creation of custom rules to allow or block specific traffic based on IP addresses, ports, and protocols.
- Predefined Rules: Comes with a set of predefined rules for common applications and services, simplifying the configuration process.
- Application Control: Controls which applications are allowed to access the network, preventing unauthorized software from communicating.
4. Security and Protection
- Intrusion Detection: Includes intrusion detection capabilities to identify and block suspicious activities and potential threats.
- Port Scanning: Detects and prevents port scanning attempts, safeguarding against unauthorized network probing.
- Logging and Alerts: Logs all network activity and generates alerts for suspicious or blocked activities, enabling users to respond promptly to potential threats.
Password: 123